After unlocking the bootloader on my S10e I was unable to flash an unofficial Lineage OS 17.1 (Android 10) ROM to my device. I was originally on the stock AT&T ROM which STILL (January 2021) hasn't been updated to Android 10. Most other carriers have released Android 10 for their S10 devices but AT&T not only is shipping devices with fully locked bootloaders but also aren't supporting their customers with updates. With the power of modern technology and a little ingenuity we can right these wrongs.
First you'll need an unlocked bootloader so you can flash your device with Odin. I was able to purchase an unlock for my S10e from SamPWND (read my article here) but if you already have an unlocked bootloader you're ready to flash.
Two tools are required for this update process. Frija for downloading the updated stock Android 10 ROM and Odin3 to flash your device in download mode.
Frija Download: https://forum.xda-developers.com/t/tool-frija-samsung-firmware-downloader-checker.3910594/
Odin3 Download: https://forum.xda-developers.com/t/patched-odin-3-13-1.3762572/
Downloading Stock Android 10
An Android 10 Custom Rom requires your device to already be on Android 10 to flash it successfully. Since AT&T hasn't released a version of Android 10 I used Frija to download a clean ROM. I needed to use the SPR (Sprint) code in CSC which specifies the carrier. Check for updates, then download. Frija will decrypt the update so you can use it with Odin.
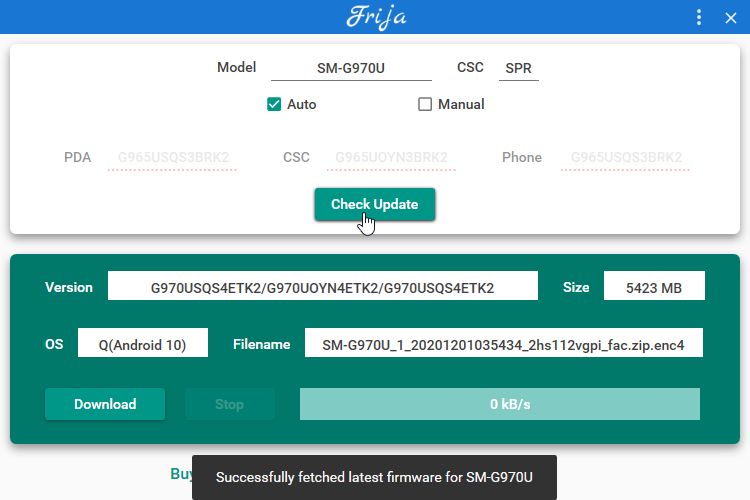
Once you've downloaded the update unzip it somewhere. You will have a few files that match the input fields in the Odin3 tool. Put your device into Download Mode and set each of the fields to their matching file from the update. Even the BL field. This will NOT relock your bootloader. You can flash TWRP or a custom recovery after you have verified you can boot into Stock Android 10.
Flash and Wait. Then your device should reboot into Android 10!